Hello There!
As you might know, NIST has acknowledged that large-scale quantum computers will threaten the security of its approved public-key algorithms.
In particular, NIST-approved digital signature schemes, key agreement using Diffie-Hellman (DH) and Menezes-Qu-Vanstone (MQV), and key agreement and key transport using Rivest–Shamir–Adleman (RSA) may need to be replaced with secure quantum-resistant (or “post-quantum”) counterparts (This project had been started since 2016).
In reference to : Transitioning the Use of Cryptographic Algorithms and Key Lengths
The goal of post-quantum cryptography (also called quantum-resistant cryptography) is to develop cryptographic systems that are secure against both quantum and classical computers, and can interoperate with existing communications protocols and networks.
NIST encourages implementers to plan for cryptographic agility to facilitate transitions to quantum-resistant algorithms where needed in the future.
In public-key cryptography, RSA is one of the most widely known and used for encryption, decryption, and digital signatures, which allows us to know that our information is secure, came from the source we think it came from, and hasn’t been tampered with.
1. WHY NIST RECOMMENDS TO PREPARE POST-QUANTUM CRYPTOGRAPHY (PQC) ?
In recent years, there has been a substantial amount of research on quantum computers – machines that exploit quantum mechanical phenomena to solve mathematical problems that are difficult or intractable for conventional computers.
If large-scale quantum computers are built, they could break many existing public-key cryptosystems.
What?? So all the public-key and all stuffs that use can easily break by PQC? Is that true?
For example (this is for example only), let’s check on security part of the website that i usually buy a goods, its tokopedia.
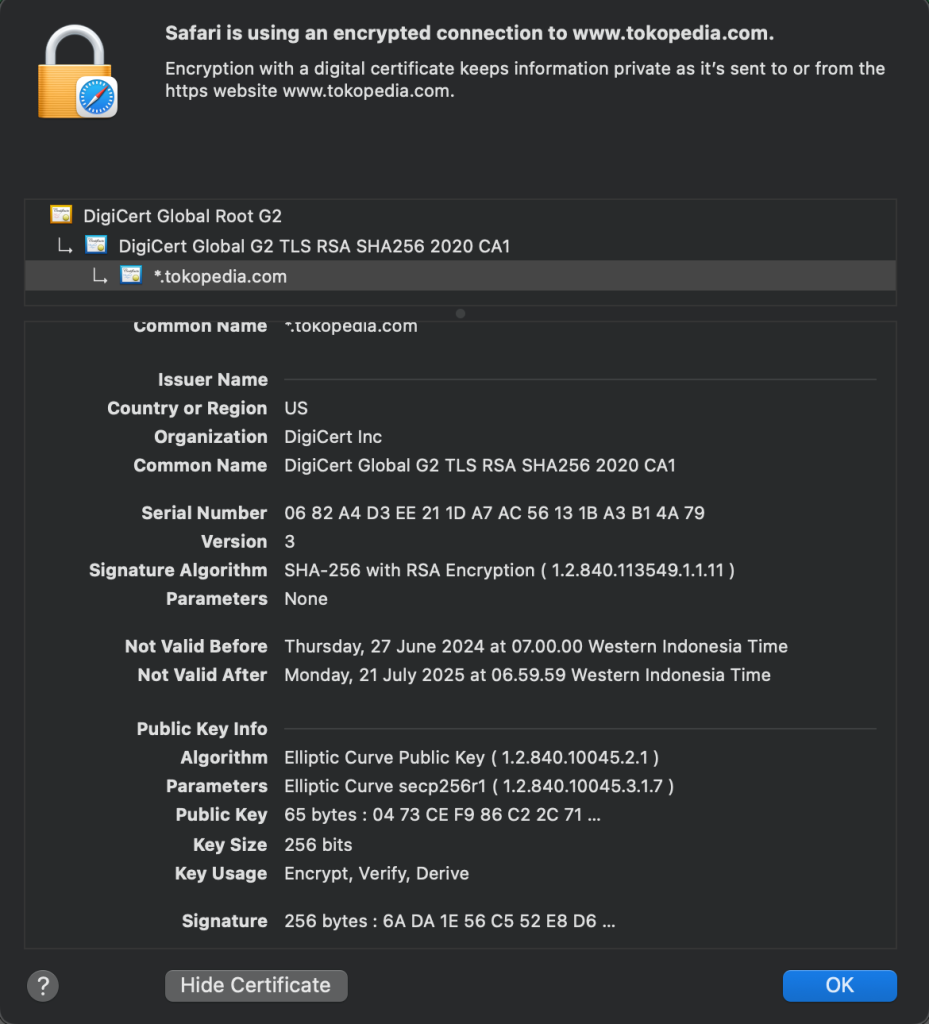
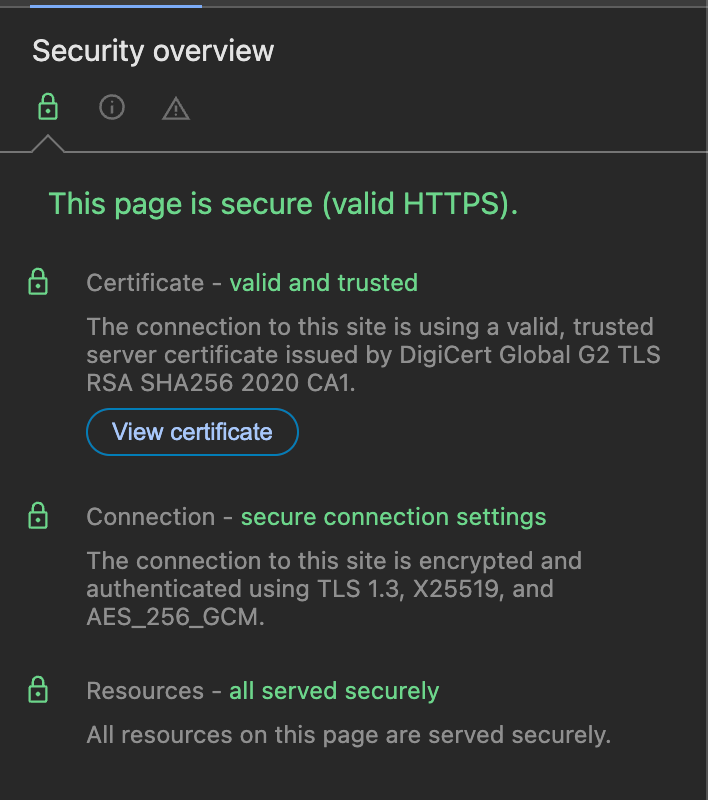
Tokopedia uses ECDHE (Elliptic curve Diffie-Hellman) signed using RSA keys.
Both quantum breakable. Other quantum breakable algorithms include: DSA (Digital Signature Algorithm) schemes and the Diffie-Hellman key-exchange protocol.
What about AES? As you see, Tokopedia used AES-256 to encrypt, which is good!
2. PQC STANDARDIZATION PROCESS
According to NIST announcement, four algorithm had been standardized.
There is a standard which FIPS 203, FIPS 204 and FIPS 205.
| Public-Key Encryption / Key Encapsulation Mechanism (KEMs) | Digital Signatures |
| CRYSTALS-KYBER | CRYSTALS-Dilithium FALCON SPHINCS+ |
3. CHECK YOUR DAILY ACTIVITY, WHAT IS RELATION IN ALL ABOUT?
Now, do you have a bank account? that always do a transaction in daily basis? or maybe you use your bank account on your mobile app to check your balance when pay day is coming? do you use username and password on many website?
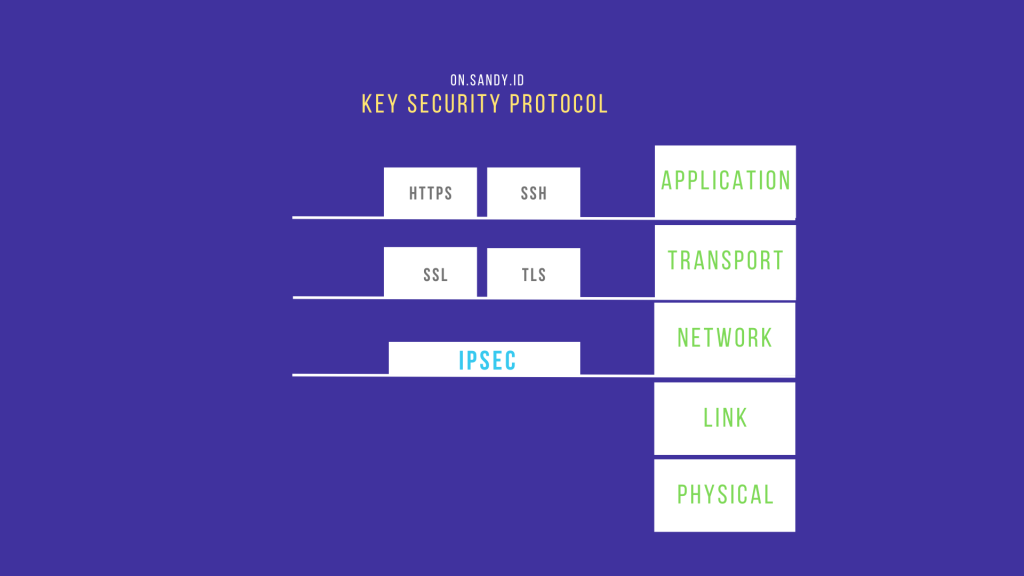
Image figure : Key security layer in different protocol
Both symmetric and asymmetric algorithms are at the core of modern systems like SSL, VPN, HTTPS to communicate securely over the internet. Or even you might use IKE, SSH, IPSec, DNSSEC for another purpose. No doubt about it.
The information you provide when logging into your account or making an online purchase is likely secured and verified by an algorithm that may be vulnerable to quantum-based attacks.
4. WHAT NEXT? WHAT CAN COMPANIES AND PEOPLE DO NOW TO PROTECT THEMSELVES FROM FUTURE ATTACKS?
The question of when a large-scale quantum computer will be built is a complicated one.
Some engineers predict that large quantum computers could break most public key schemes. Historically, it has taken almost two decades to deploy our modern public key cryptography infrastructure.
Therefore, regardless of whether we can estimate the exact time of the arrival of the quantum computing era, we must begin now to prepare our information security systems to be able to resist quantum computing.
If you are an organization
Don’t wait for the standard to be done. Start inventorying your most important information. Ask yourself what is that data that an adversary is going to want to break into first.
Since the initial quantum computers will be costly to operate and maintain, it’s important to assess which of your information is most critical and whether its encryption is vulnerable.
If it is, establish priorities for adopting quantum-resistant encryption as you plan infrastructure upgrades over the next few years. Then, begin prioritizing and strategizing to ensure you’re prepared to implement the new standards as they become available.
For those of us in the consumer space
You’re going to rely on your tech providers to roll this out for us. Our IT product and service providers are ready, and they’re itching to get these new standards out there and put them to work.
If you want to learn about my other note, you might visit here for code and database section, it is still related on what you wanted to learn in all about technology itself.
That’s all folks! Happy learning as always! 🥰😍




Leave a Reply